Command Prompt itself is a DOS command in the Windows OS that can facilitate the user in navigating Windows either by means of on-line or off line. Meanwhile, for users of the Linux OS, the same feature is referred to as a terminal CMD.
CMD command Frequently Used by Hackers
As a computer user, you should know the closer CMD and understand the work steps and use. To open a Command Prompt quickly, use the keyboard combination Windows key + R with a concurrent manner. Thus, it can open the Run dialog box. After that, write cmd and press enter then CMD will open. Written from TechWorm, the Command Prompt commands are often used by hackers in action.
1. Ping
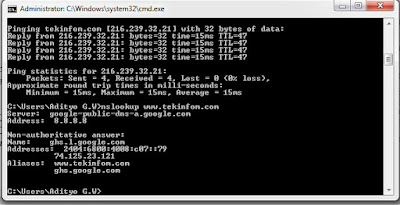
Ping command is often used to study the problem in the network. The main benefits of the Ping ie check whether ip / domain specific alive or dead. Ping itself has a lot of parameters and benefits are often used by hackers. By way of default, Ping, Windows will send four packets, for example, ping x. x. x. x (x ie IP address). You can try pinging 8. 8. 8. 8 has a Google or ping www. google. com if you do not understand Google IP.
2. Nslookup
Nslookup has many benefits. One of her is used to know the ip of the domain. Beyond that, nslookup often used to diagnose network problems associated with DNS.
Say you understand you understand the site's URL, but you do not know its IP address, you can know the nslookup command in CMD. For example, by typing nslookup www. google. com (www. google. com are examples of websites that want you to recognize IP).
3. Tracert
CMD command Tracert
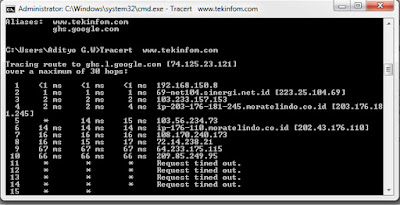
Commands traceroute tracert other words used to search for the path to the data packets ip / specific host on the Internet. This command is in some kind of network device router, wireless AP, Modem, Windows, Linux, and servers.
Although this tool is on each network device, semasing name and slightly different command parameters. For example, tracert x. x. x. x (x ie IP address) or tracert www. google. com.
4. ARP
CMD command ARP
The command ARP or Address Resolution Protocol is a protocol that is responsible for finding out the Mac Address or the hardware address of the host that is incorporated in a LAN network. Certainly, using or based on the IP address configured on the host-related. In OSI, this protocol works at Layer 2 and Layer 3.
5. Route
CMD command Route
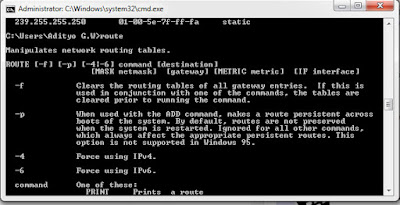
The route command is used to create new paths (routing) on the computer to a network, generally on a LAN or WAN. Beyond that, you can tell the system the highway network, the path info host, gateway, and network destination.
6. Ipconfig
CMD command ipconfig
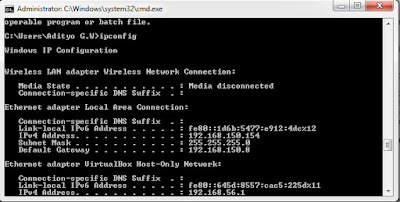
Ipconfig command is used to view the network information or IP information attached to the network adapter. Indeed ipconfig benefits not only that, there are still other functions that are so useful to handle network troubleshooting or set the network again, especially those using the network with DHCP.
7. Netstat
CMD command Netstat
Netstat command has managed to bring the network connection statistics to a central computer that you use. Netstat can be equated with the task manager. The difference, the system presents a task manager and applications that way, being Netstat bring the service network being used, along with additional information such as IP and its port.
What is your opinion? Despite the appearance of CMD is so simple, but the benefits are so amazing is not it? It is most often used commands CMD in action, the benefits were abused hackers to achieve their goals.



0 Response to "This is the command CMD Frequently Used Hacker"
Post a Comment